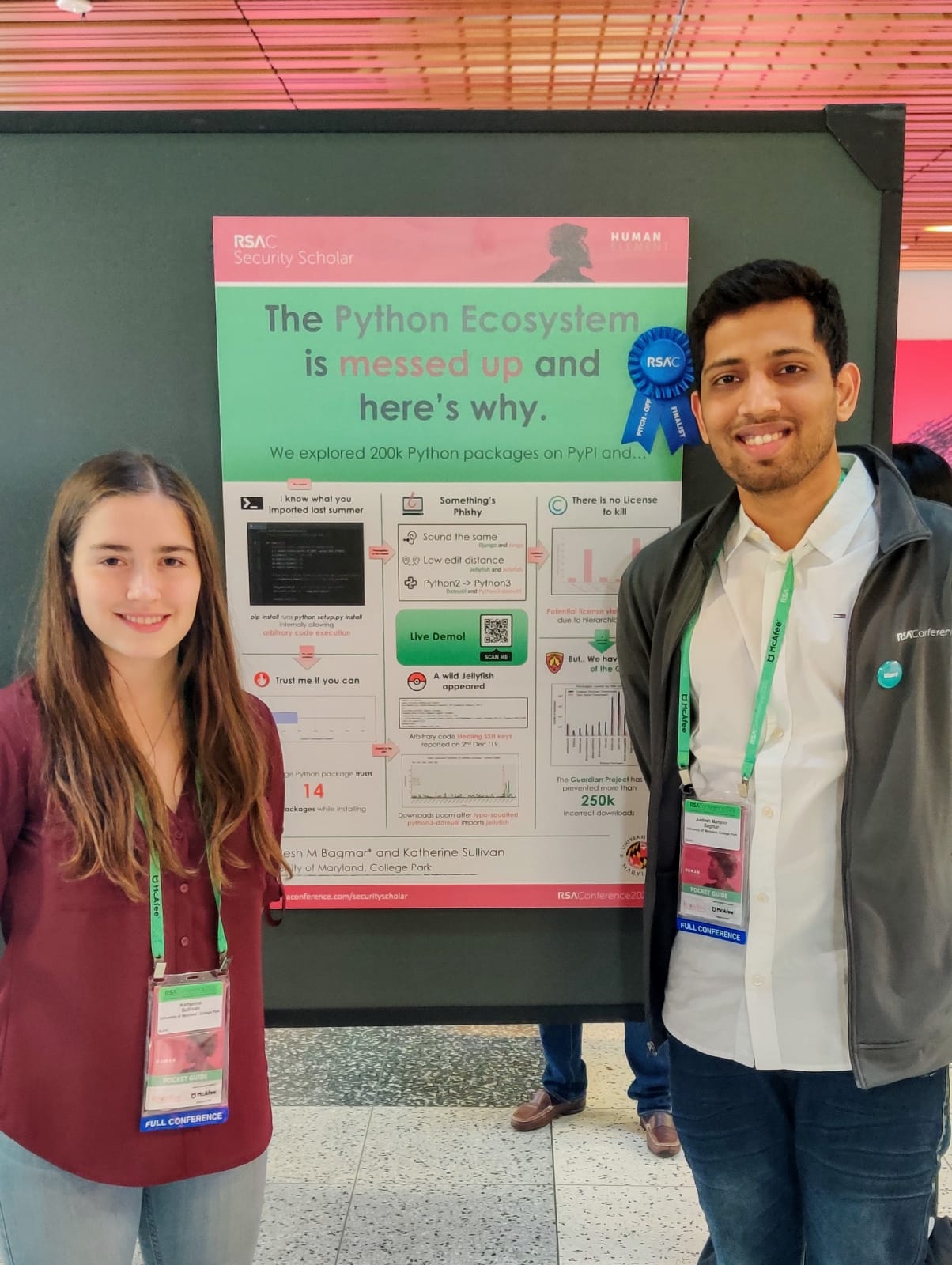
The Python ecosystem is messed up and here's why
A study of security vulnerabilities in the Python Ecosystem.
The popularity of Python has risen rapidly over the past 15 years. It is a major language in some of the most exciting technologies today. This popularity has led to a large ecosystem of third party packages available via the pip package registry which hosts more than 200,000 packages. These third party packages can be reused by simply importing the package after installing using package managers like pip. The ease of reuse of third party software comes with security risks putting millions of users in danger. In this project, we study the ecosystem to analyze this threat.
The mature ecosystem of Python has multiple weak spots that we highlight in our project. First, we demonstrate how trivial it is to exploit the Python ecosystem. Then, we systematically analyze dependencies amongst packages, maintainers and publicly reported security issues. Most attacks are possible only if users install malicious packages. We thus try to analyze and evaluate different methods used by attackers to force incorrect downloads. We quantify our ideas by estimating the potential threat that can be caused by exploiting a popular Python package. We also discuss methods used in the industry to defend against such attacks
Other Mentions:
Beware of copy pasting code from Stackoverflow, or installing packages recommended directly from Python's PyPi -- a smart hacker used this attack to steal ssh keys from 21,000+ developers!
— Nirant (@NirantK) February 27, 2021